Using the WS-Malicious Pattern Detection Policy
Learn about the WS-Malicious Pattern Detection Policy and policy configuration options.
For information about using policies in the context of the Community Manager developer portal, see Business Policies.
Table of Contents
- About the WS-Malicious Pattern Detection policy
- Creating a WS-Malicious Pattern Detection policy
- Configuring a WS-Malicious Pattern Detection policy
- Viewing a WS-Malicious Pattern Detection policy
- Activating a policy
- Attaching a policy
- Examples: out-of-the-box SOAP XPath Injection policy
About the WS-Malicious Pattern Detection policy
The WS-Malicious Pattern Detection policy is very similar to the HTTP Malicious Pattern Detection policy, but it is tailored for SOAP messages. In particular, the SOAP body and SOAP headers can be handled differently. You can use the WS-Malicious Pattern Detection policy for SOAP message (transmitted over HTTP), but the envelope has no special meaning and would be treated as any XML content.
Creating a WS-Malicious Pattern Detection policy
The first step in creating a policy is to define the basic policy information.
To add an operational policy
- Go to Workbench > Browse > Organization, and select Policies > Operational Policies. The Policies Summary is displayed.
- Click Add Policy.
- Choose the policy type and click Next.
- Specify a name (required) and description (optional) and click Finish. At the Completion Summary, click Close. The Add Policy Wizard creates a draft policy instance that you can then configure on the Policy Details page.
For more information, see Add Policy.
Configuring a WS-Malicious Pattern Detection Policy
The Modify WS-Malicious Pattern Detection Policy screen allows you to modify the required content options for the WS-Malicious Pattern Detection policy.
To configure a WS-Malicious Pattern Detection policy
- Go to Workbench > Browse > Organization and select the Policies > Operational Policies folder. The Policies Summary is displayed.
- Find the policy on the list and double-click to go to the Details page for the policy.
- In the second panel, click Modify to access the Modify WS-Malicious Pattern Detection Policy page, as shown below.
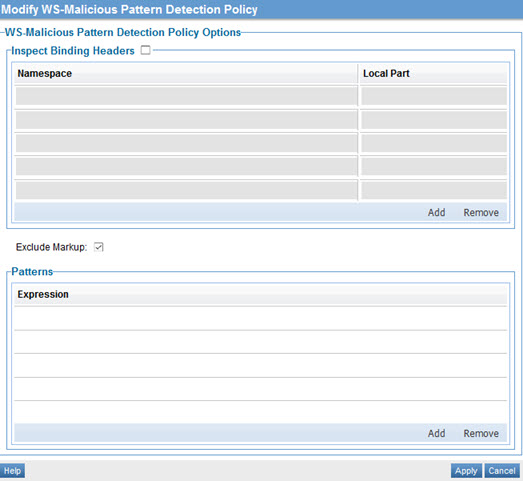
- Specify values. For information about the fields, refer to WS-Malicious Pattern Detection policy options below.
- When done, click Apply.
WS-Malicious Pattern Detection policy options
The Modify WS-Malicious Pattern Detection Policy wizard has only one page. It includes the options listed below.
- Inspect Binding Headers
- Optionally, SOAP headers can be scanned for patterns. By default, if you select this option, all headers will be scanned. To scan only certain headers, add the header names in the table.
- Exclude Markup
- If markup is excluded only the content of the properties, not the markup itself, will be scanned. For example, an XML tag will not be scanned, just the tag's value.
- Patterns
- One or more regular expression patterns to scan for. Any match will cause the message to be rejected. For more information about using regular expressions, see Using Regular Expressions in Policies.
Viewing WS-Malicious Pattern Detection Policy Details
To view the WS-Malicious Pattern Detection policy details:
- Go to Workbench > Browse > Organization, and select Policies > Operational Policies. The Policies Summary is displayed.
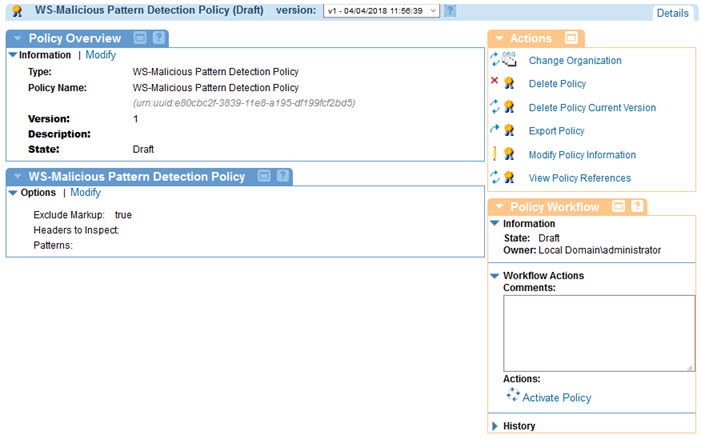
- Find the policy on the list and double-click to go to the Details page for the policy. An example is shown below.
Activating a policy
When you create and configure a policy, the policy is in Draft state. When the policy configuration is complete, activate the policy: click Activate Policy and then confirm. See Activate a Policy.
A policy in Draft state is not available for general use. Once you activate the policy, it is in Active state and is available for use.
Attaching a policy
To use the policy, go to the Policies folder in the respective organization and attach the policy to a web service, binding, or binding operation.
Examples: out-of-the-box SOAP XPath Injection policy
The following examples illustrate an out-of-the-box SOAP XPath Injection policy which is an application of the WS-Malicious Pattern Detection policy.
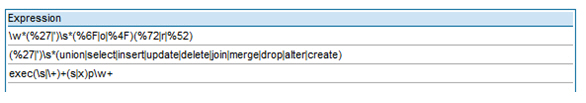
Regular Expressions:
In the example below, the regular expression matches XPath symbols.
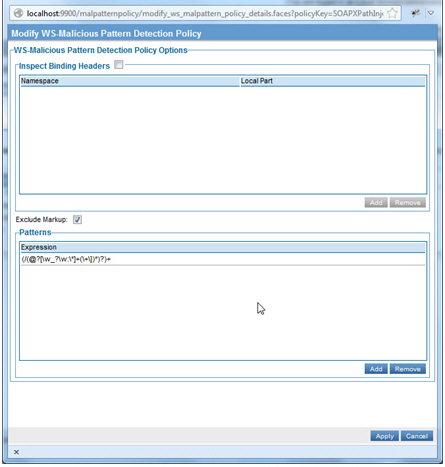
For more information about using regular expressions, see Using Regular Expressions in Policies.
SQL Expressions:
A SOAP SQL detection policy is also included out-of-the-box. Its expressions match SQL symbols and keywords, as shown below.