Organization Security/Roles
Manage security roles associated with an organization on the API platform.
Table of Contents
- How do I manage security for my organization?
- How do I assign security roles to users and groups for my organization?
- How do I assign LDAP domain users and groups for my organization?
- How do I assign SAML Web SSO domain users and groups for my organization?
- What are the default roles for the API platform?
- Use case: creating a custom role with Monitor permission only
How do I manage security for my organization?
The API platform allows you to assign one or more specific roles to users.
All roles defined in the underlying Policy Manager infrastructure, either for the root organization or for the current business organization, are available to be assigned to users in your organization.
This accommodates many use cases and allows you to assign rights to create, view, modify, and delete resources in your organization, to a very fine level of granularity. You can control user access rights to a much more detailed level than the Developer, API Admin, Business Admin, and Site Admin roles supported in versions of the API platform prior to version 8.3.
You can assign access roles to specific users in your organization via the Security page. See How do I assign security roles to users or groups for my organization?
You can also add roles. Currently, new roles must be added in Policy Manager, and are then available for selection in the API Platform UI. Roles added at the root organization level are available for all organizations; you can also add one or more roles for a specific organization, and they are available only for that organization.
For information on adding roles in Policy Manager, refer to the Policy Manager help.
How do I assign security roles to users and groups for my organization?
You can assign and remove roles to specific users and groups in your organization, via the organization's Security page.
To assign security roles to users and groups
- In the Community Manager developer portal, go to the Organizations List (see To access the Organizations List).
- Find your organization on the list, and then click the title to view the Details page for the organization.
- On the left navigation bar, choose Security. In the right pane, the Role Memberships page, all roles currently available to the organization are displayed.
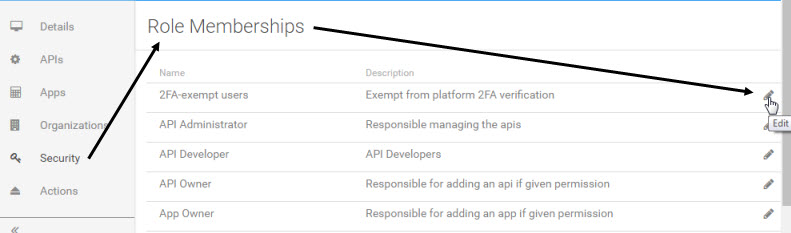
- On the list, find the role you want to assign, and click the Edit (pencil) icon to the right. The {role name} - Users/Groups page has two panes:
- Left pane has a search bar to help you identify one or more users or groups you want to assign the role to.
- Right pane lists users or groups currently assigned to the role.
- In the left pane, use the dropdown menu to select the domain, user, or group to assign them to a role. In the text box, type the name of the user or group to search in the selected domain, and click Go. The name of the users or groups will be displayed in the Results list.
- Click to select the checkbox for the user or group name from the Results list to assign them a role. Click Assign.
- The user or group name appears in the Assigned Users/Groups list. Click Save.
- To remove users or groups, in the right pane, click to select the checkbox for the user or group name from the Assigned Users/Groups list and click Remove.
How do I assign LDAP domain users and groups for my organization?
Valid in Version: 2022.1.3 and later
To assign the external LDAP domain users and groups in your organization, follow the instructions:
Prerequisites
Before you begin:
-
Configure an LDAP Directory or Active Directory Identity System. See, Configure Directory Server (Active Directory) Identity System.
-
Enable a domain login for users to log in to the platform. See, How do I enable a domain for login?
Configuration on Community Manager
To assign the users and groups
- In the Community Manager developer portal, go to the Organizations List (see To access the Organizations List).
- Find your organization on the list, and then click the title to view the Details page for the organization.
- On the left navigation bar, choose Security. In the right pane, the Role Memberships page, all roles currently available to the organization are displayed.
- On the list, find the role you want to assign, and click the Edit (pencil) icon to the right. The {role name} - Users/Groups page is displayed.
- Use the dropdown menu to select LDAP domain and User or Group to assign them to a role. To assign:
User: Search for users in the selected domain and assign them to the role. ClickGo.
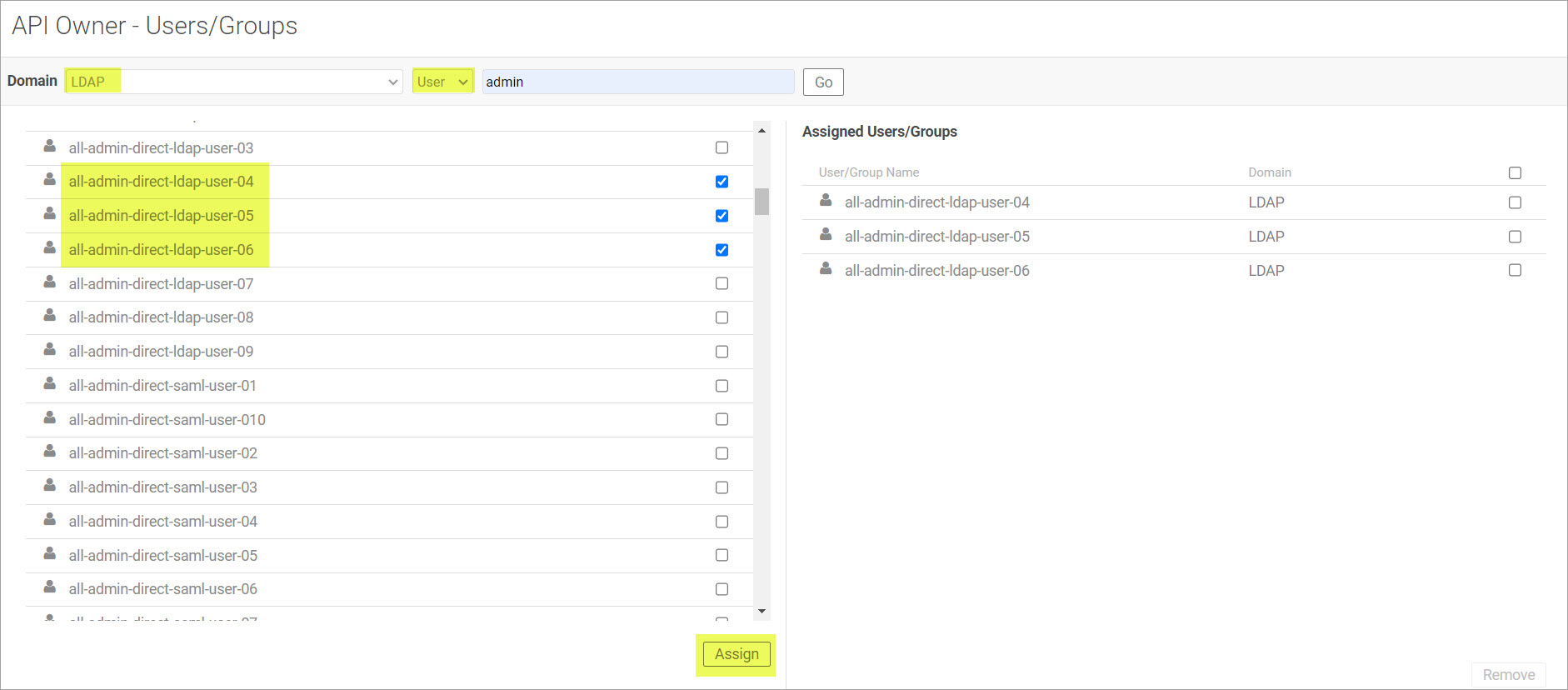
Group: Search for groups in the selected domain and assign them to the role. Click Go.
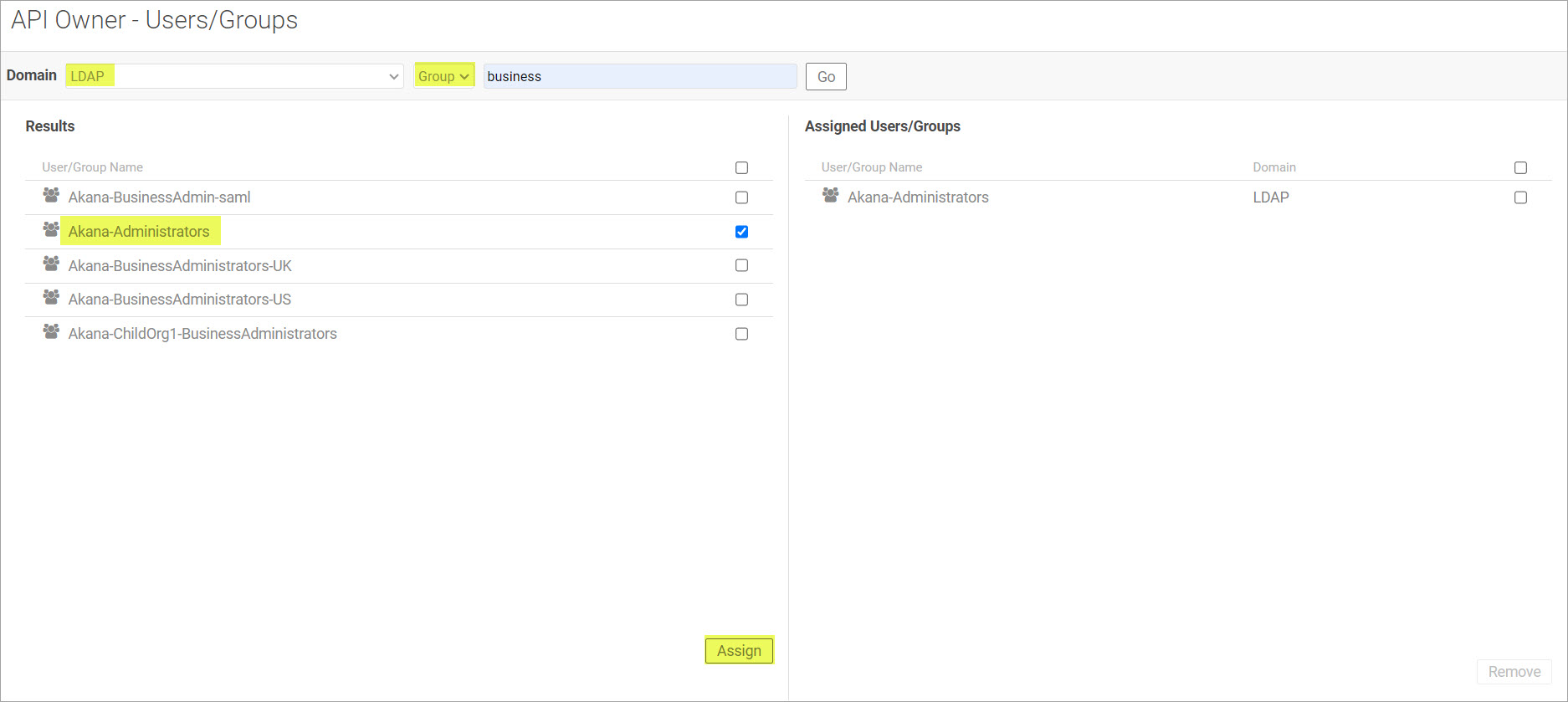
- Click to select the checkbox for the user or group name from the Results list to assign them a role. Click Assign.
- The user or group name appears in the Assigned Users/Groups list. Click Save.
How do I assign SAML Web SSO domain users and groups for my organization?
Valid in Version: 2022.1.3 and later
To assign the external SAML Web SSO domain users and groups in your organization, follow the instructions:
Prerequisites
Before you begin:
-
Configure the SAML Web SSO domain. See, Setting Up the SAML Web Browser SSO.
-
Configure the Identity Provider to send additional attributes for Group Memberships. The attribute mapping for groups must be done in Policy Manager to match the "Group Memberships" attribute name, which will be sent in the SAML Assertion response. See, Configure the SSO domain in Policy Manager.
-
Enable a domain login for users to log in to the platform. See, How do I enable a domain for login?
Configuration on Community Manager
To assign the users and groups
- In the Community Manager developer portal, go to the Organizations List (see To access the Organizations List).
- Find your organization on the list, and then click the title to view the Details page for the organization.
- On the left navigation bar, choose Security. In the right pane, the Role Memberships page, all roles currently available to the organization are displayed.
- On the list, find the role you want to assign, and click the Edit (pencil) icon to the right. The {role name} - Users/Groups page is displayed.
- Use the dropdown menu to select the SAML domain and User or Group to assign them to a role. To assign:
- User: Search for users that have previously logged into Akana via the selected domain and assign them to the role.
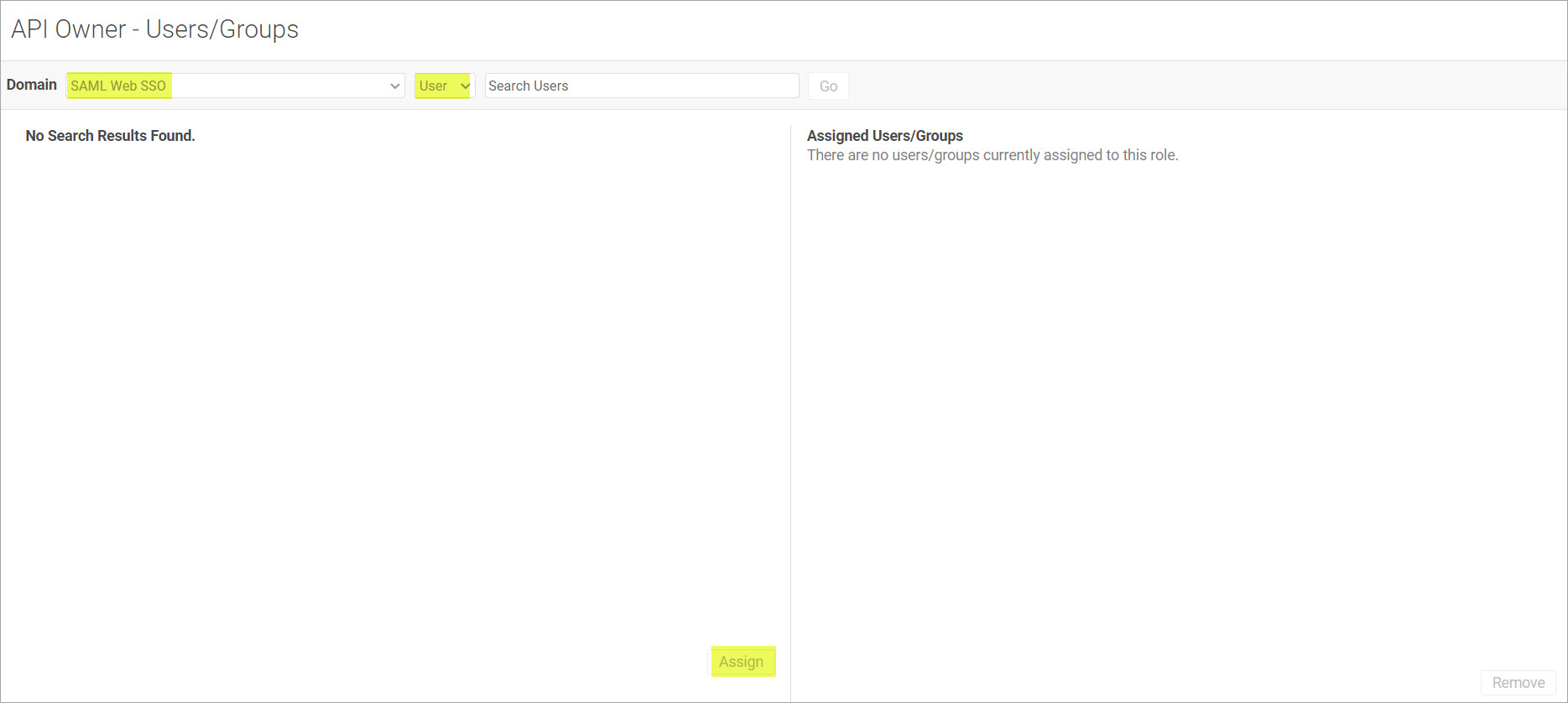
- Group: Provide the exact value of the group attribute in the SAML assertion for a user that is mapped to the role.
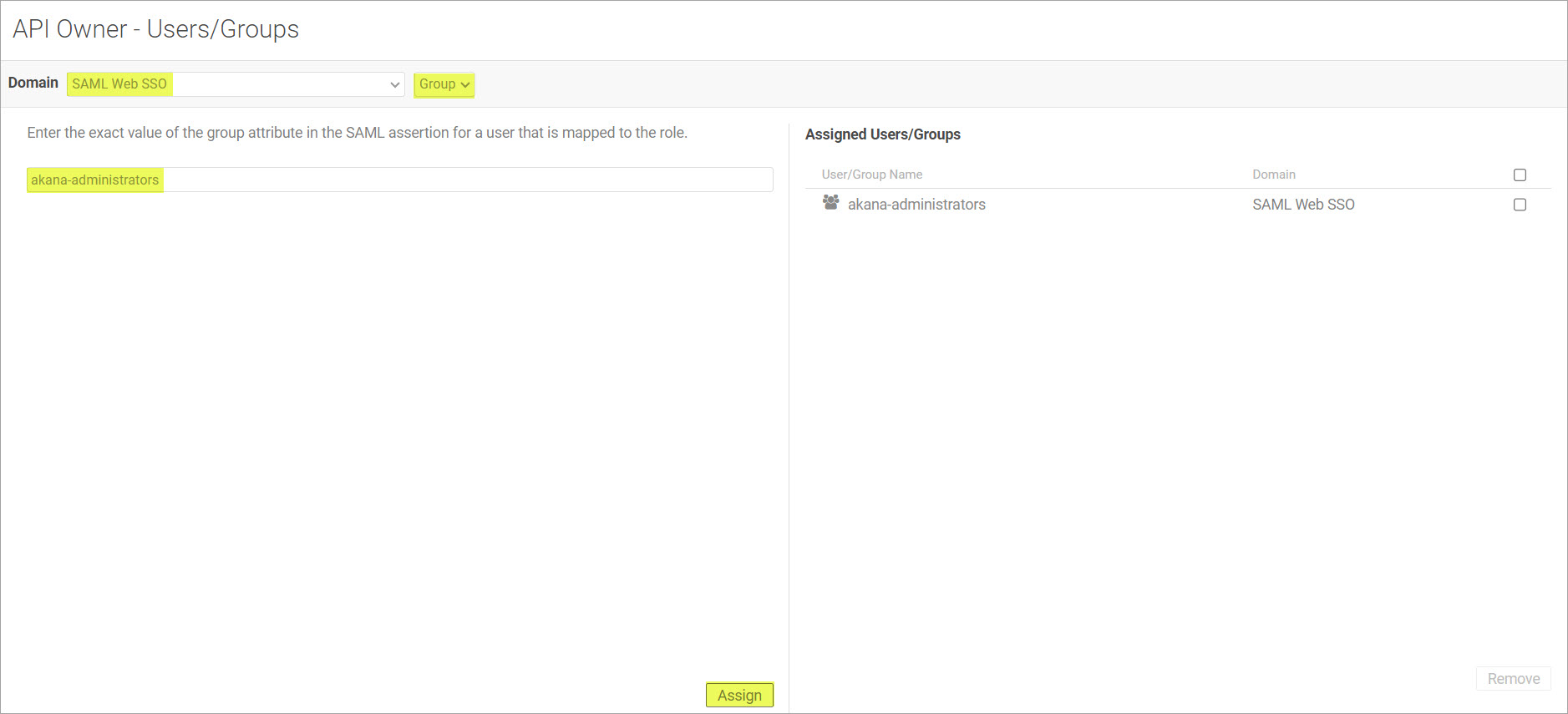
- User: Search for users that have previously logged into Akana via the selected domain and assign them to the role.
- Click to select the checkbox for the user from the Results list to assign them a role. Click Assign.
- The user or group name appears in the Assigned Users/Groups list. Click Save.
What are the default roles for the API platform?
In the Community Manager developer portal, you can manage roles for the platform users who are part of your business organization, as explained in How do I assign security roles to users or groups for my organization?
The summary below gives you the basic definition for each of the default roles. Note that your platform implementation might already include some customization of roles, in the underlying infrastructure. The definitions below are the defaults.
Default roles
- 2FA-exempt users
- A user who is exempt from platform 2FA verification. Even if two-factor authentication is required for platform users, it is not required for users with this role assigned.
- API Administrator
- Responsible for managing APIs for the organization. The API Admin has full permission for operations relating to all APIs in the organization, including adding, modifying, and deleting APIs, API versions, and API implementations.
- API Administrator and API Admin are the same role.
- Note: A user assigned the API Administrator role in the context of a business organization, who is not invited to a specific API, does not have permission to manage API Admins, such as adding or removing other API Admins. Only a user invited to a specific API has those permissions. For details, see What API management capabilities are available to the API Admin in the platform?
- API Approver
- Responsible for approving APIs for publishing.
- API Developer
- API Developers have read-only access to the API.
- API Owner
- Responsible for adding an API. In a scenario where a basic platform user cannot add APIs, a user who is assigned the role of API Owner can add APIs. The user who creates the API becomes the first API Admin.
- API Platform Users
- Users who have signed up for the Community Manager developer portal by creating an account, or have been added by a Site Admin and have then activated the account.
- App Team Member
- Responsible for managing an app. Each app team member has full permission for operations relating to the app, including adding, modifying, and deleting apps and app versions as well as adding or removing other app team members.
- Developer
- Responsible for registering and building web services. This role is used by the underlying infrastructure, not by the Community Manager developer portal. Do not assign or change this role in the Community Manager developer portal.
- Federation Member
- A member of a tenant federation, in a scenario where federation is in effect for the platform implementation.
- Group Administrator
- Has full administrator rights for the specific group; for example, can add, remove, promote, or demote any group member, and can delete the group. For details, see What can a group Admin do?
- Group Leader
- Has Group Leader rights; for example, can promote or demote Group Members and other Group Leaders. For details, see What can a group Leader do?
- Group Member
- Has Group Member rights; for example, can invite others to join the group. For details, see What can a group Member do?
- Guest
- An anonymous user who is using the Community Manager developer portal without logging in. Guests have view-only access to public content. If an API is set to allow anonymous access (depends on API implementation settings), the anonymous user can test the API in Test Client.
- Infrastructure Manager
- Responsible for installing containers, virtualizing services, and deploying services to containers. This role is used by the underlying infrastructure, not by the Community Manager developer portal. Do not assign or change this role in the Community Manager developer portal.
- LC Administrator
- Has Administrator rights (full add/modify/delete/read permission) for all Lifecycle Coordinator functionality.
- LC User
- Has permission for general use of Lifecycle Coordinator functionality.
- Model Administrator
- Responsible for managing model objects in the Model Library. For more information, see What are the duties of the Model Administrator?
- Model Designer
- Responsible for designing model objects in the Model Library. For more information, see What are the duties of the Model Designer?
- Operation Manager
- Responsible for developing security and monitoring policies and assigning them to services and organizations.
- Organization Administrator
- Responsible for adding, modifying, and deleting organizations and managing services, policies, and containers within a Policy Manager organization (underlying infrastructure). Do not assign or change this role in the Community Manager developer portal. To allow a user to modify organizations in the Community Manager developer portal, assign the Business Administrator role.
- Policy Administrator
- Responsible for adding, modifying and deleting policies within an organization.
- Provision Manager
- Responsible for approving app/API contracts in any scenario where approval is required (depends on API implementation settings).
- Security Administrator
- Responsible for granting access to the Workbench for an organization, to users and user groups. This role is used by the underlying infrastructure, not by the Community Manager developer portal. Do not assign or change this role in the Community Manager developer portal.
- Tenant Business Administrator
- Responsible for managing the APIs within the entire tenant installation.
- Tenant Manager
- Has full rights and permissions to manage the tenant installation.
Use case: creating a custom role with Monitor permission only
You might want to create a custom role so that certain users can have Monitor permission, to view an API's analytics information, without those users being able to view and modify private APIs unless invited.
You can do this, but you must define the new role in Policy Manager, the underlying infrastructure for the Community Manager developer portal.
When you follow the steps, you can create a role that:
- Cannot edit APIs
- Cannot view private APIs unless specifically invited to have visibility of the API
- Can monitor analytics for all APIs
For instructions to create this custom role, see Use case: creating a custom role with Monitor permission only (Policy Manager documentation). The use case information includes instructions for assigning the role to users in Policy Manager, but you can also assign the role in the Community Manager developer portal: see How do I assign security roles to users for my organization? above.




